5 ways to detect a phishing email
Phishing is one of the most dangerous methods of cyber-crime. It uses trickery and deceptive messages to lure victims into clicking bogus links, downloading malicious attachments or sending sensitive information.
Despite what people think they know about Phishing, they consistently fall victim. According to Verizon’s 2019 Data Breach Investigations Report, 32% of all cyber-attacks involved phishing. Here is a list made by ITgovernance on how to spot and protect yourself against Phishing emails:
1. The message is sent from a public email domain
The picture below is of a scam email that is sent from a public domain.
No legitimate organization will contact you from an address that ends ‘@gmail.com’. Not even Google.
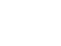
With the exception of independent workers, every organization will have its own email domain and company accounts. For example, emails from Google will read ‘@google.com’. If the domain name (the bit after the @ symbol) matches the apparent sender of the email, the message is probably legitimate. The best way to check an organization's domain name is to type the company’s name into a search engine. Also always look at the email address as it is usually the best indicator of a false email. The example below is an almost flawless scam email pretending to be from PayPal and one of the only things to give it away is the email address.
2. Look for grammatical mistakes, not spelling mistakes
When crafting phishing messages, scammers will often use a spellchecker or translation machine, which will give them all the right words but not necessarily in the right context. Some may also use a font or font size that is not standard practice such as the one below which contains a 9px font.
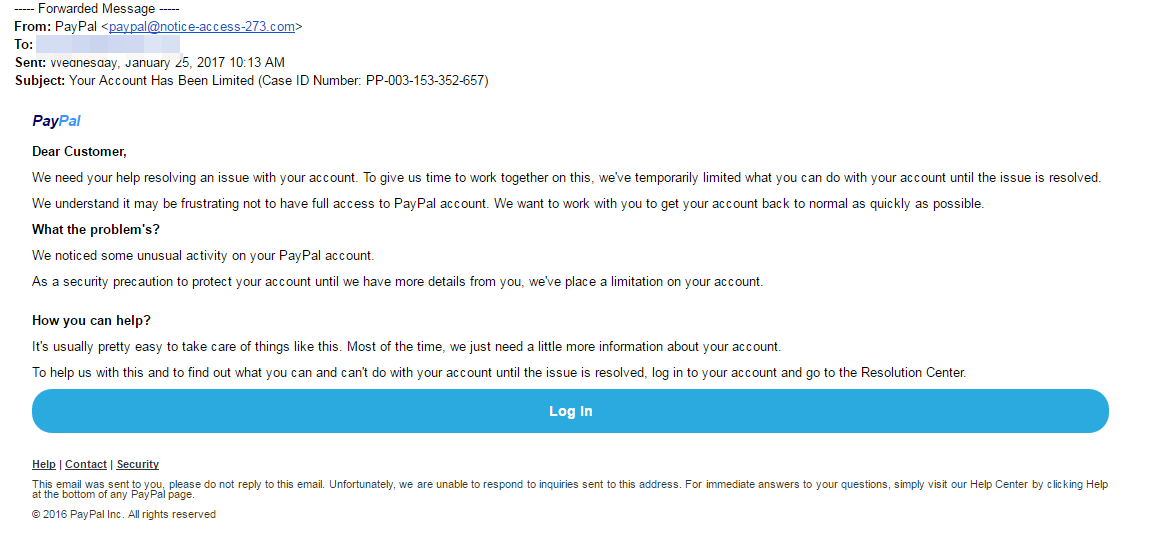
Take this example of a scam imitating Windows:
No individual word is spelled incorrectly, but the message is full of grammatical errors that a native speaker wouldn’t make, like “We detected something unusual to use an application”, and a string of missed words, such as “a malicious user might trying to access” and “Please contact Security Communication Center“.
These are consistent with the kinds of mistakes people make when learning English. Any supposedly official message that’s written this way is almost certainly a scam.
That’s not to say any email with a mistake in it is a scam, though. Everyone makes typos from time to time, especially when they’re in a hurry.
It’s therefore the recipient’s responsibility to look at the context of the error and determine whether it’s a clue to something more sinister. You can do this by asking:
• Is it a common sign of a typo (like hitting an adjacent key)?
• Is it a mistake a native speaker shouldn’t make E.g. words used in the wrong context?
• Is this email a template, which should have been crafted and copy-edited?
• Is it consistent with previous messages I’ve received from this person?
If you’re in any doubt, you should look for examples of the other clues we list here or try to contact the sender using an alternative method (in person, by phone, via their website, an alternative email address or through an instant message client).
3. It includes suspicious attachments or links
Phishing emails come in many forms, but the one thing they all have in common is that they contain a payload. This will either be an infected attachment that you’re asked to download or a link to a bogus website that requests login and other sensitive information.
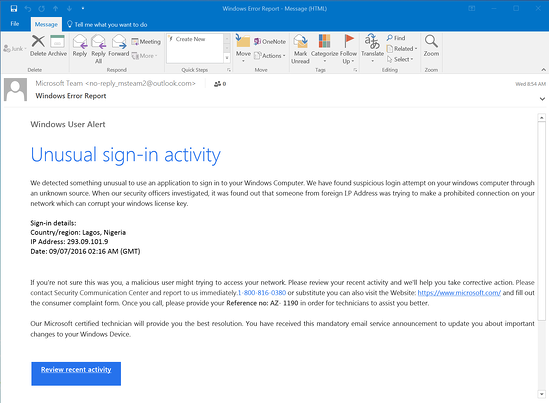
An infected attachment is a seemingly benign document that contains malware. In a typical example, like the one below, the phisher claims to be sending an invoice:
It doesn’t matter whether the recipient expects to receive an invoice from this person or not, because in most cases they won’t be sure what the message contains to until they open the attachment.
When they open the attachment, they’ll see that the invoice isn’t intended for them, but it will be too late. The document unleashes malware on the victim’s computer, which could perform any number of nasty activities
We advise that you never open an attachment unless you are fully confident that the message is from a legitimate party. Even then, you should look out for anything suspicious in the attachment.
For example, if you receive a pop-up warning about the file’s legitimacy or the application asks you to adjust your settings, then don’t proceed. Contact the sender through an alternative means of communication and ask them to verify that it’s legitimate.
4. Supicious links
You can spot a suspicious link if the destination address doesn’t match the context of the rest of the email. For example, if you receive an email from Netflix, you would expect the link to direct you towards an address that begins ‘netflix.com’.
Unfortunately, many legitimate and scam emails hide the destination address in a button, so it’s not immediately obvious where the link goes to.
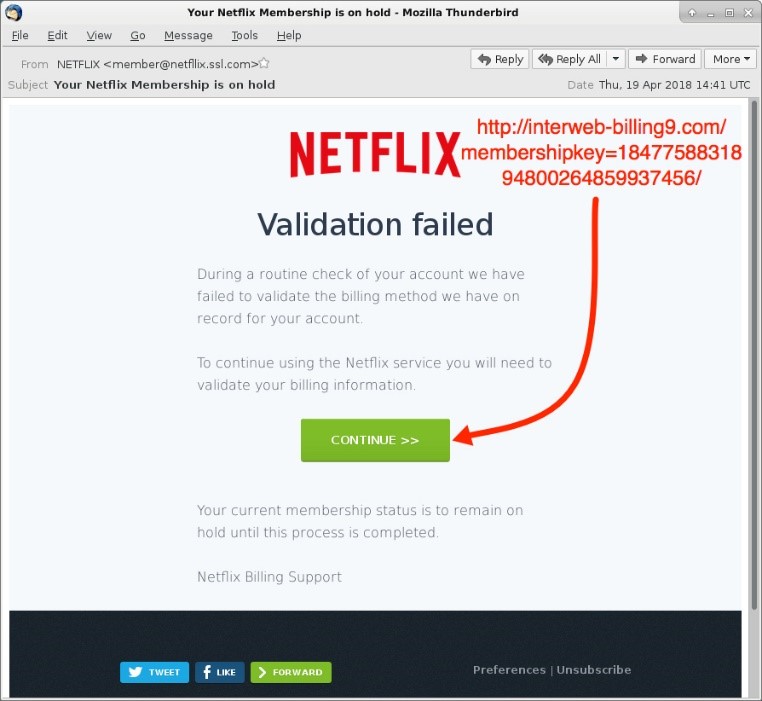
In this example, you would probably know that something was suspicious if you saw the destination address in the email. Unfortunately, the rest of the message is pretty convincing, and you might click the link without giving it a second thought.
To ensure you don’t fall for schemes like this, you must train yourself to check where links go before opening them. Thankfully, this is straightforward: on a computer, hover your mouse over the link and the destination address appears in a small bar along the bottom of the browser.
On a mobile device, hold down on the link and a pop-up will appear containing the link.
5. They will always appear urgent
The manufactured sense of urgency is equally effective in workplace scams. Criminals know that most of us will drop everything if our boss emails us with a vital request, especially when other senior colleagues are supposedly waiting on you. A typical example looks like this:
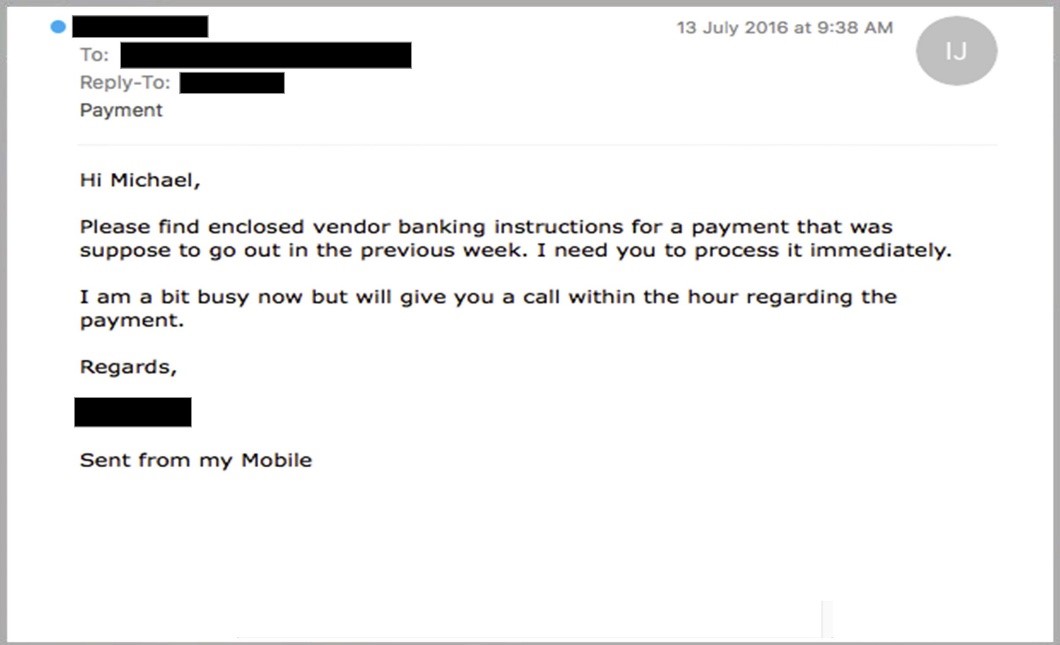
Phishing scams like this are particularly dangerous because, even if the recipient did suspect foul play, they might be too afraid to confront their boss. If they were wrong, they have not only failed to meet their boss’ urgent request but also implied that there was something unprofessional in the way the email was written.
An organization that values cyber security would accept that it’s better to be safe than sorry and perhaps even congratulate the employee for their caution. However, unless the organization explicitly tells staff to remain vigilant, they might not be willing to speak up.
If you are still unsure of an emails legitmacy after applying these tips yourself then contact us for advice using the contact details below. Alternatively open a live chat session to speak to one of experts today.
"Red Dune IT Solutions are a top notch company and I would highly recommend them."
- Anne Becket-Allen, Rosedale Funeral Home
"Speaking to my neighbours who require a new home computer system, the reaction I got was where to go? The dealer in Wymondham has gone as has the one in Long Stratton. Yes, you can purchase blind from the likes of PC world etc. But should you require advice and support then I would recommend for anyone in the south Norfolk area to contact Red Dune computer systems 01986888274 who will visit at home or business, quote, install, train and provide backup and support. In my opinion a company that does what it says it will!. To confirm, I have no financial interest in Red Dune, just a satisfied customer."
- Peter Holden